Describe the issue:
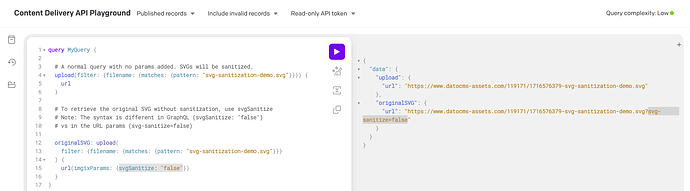
SVGs seem to be getting modified and breaking some contents recently. We noticed this started happening last week, but we’re not sure when it started.
Please let us know if there’s a way to restore those assets to their original form.
(Recommended) What’s the URL of the record or model in question?
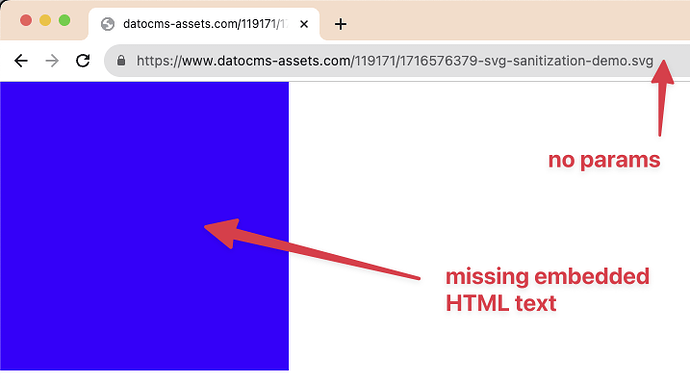
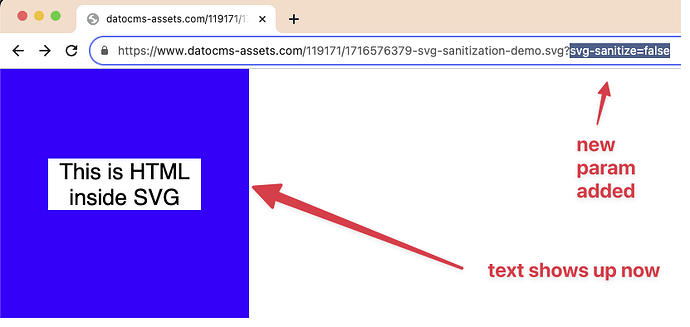
Example of one defective SVG being served:
(Optional) Do you have any sample code you can provide?
The beginning of the SVG is supposed to look like the following.
<?xml version="1.0" encoding="UTF-8"?>
<svg xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" viewBox="0 0 4208 4208">
<defs>
<style>
@font-face {
font-family: 'GatoradeBlack';
src: url(data:font/woff;base64,d09GRgABAA...
}
I’ve cropped the base64 for brevity
However, this is what we’re receiving. Note how the directives in the <svg> tag were modified and the font definition got broken altogether:
<?xml version="1.0" encoding="utf-8"?>
<svg xmlns="http://www.w3.org/2000/svg" viewBox="0 0 4208 4208">
<defs>
<style>
@font-face {
font-family: 'GatoradeBlack';base64,d09GRgABAAAAAHIY...
There are other breaking changes being applied as well. The above is one example. Please let me know if it would be helpful if I provide the original and served files.